China Issues Second Draft of Cross-Border Data Transfer Guidelines
China has issued its second draft of cross-border data transfer guidelines for public comments, as one of a series of the implementation rules for the Cybersecurity Law of China. The “Information Security Technology-Guidelines for Data Cross-Border Transfer Security Assessment” (the “Second Draft”) was jointly released by the Standardization Administration of China (SAC) and the General Administration of Quality Supervision, Inspection and Quarantine of China (AQSIQ) for public comments until October 13, 2017. Based on the Second Draft, 12 entities have participated in the drafting, among which four are private companies: Tecent, Alibaba,Ali Cloud and Ant Financial. The Second Draft has made certain changes and added clarification to the First Draft Guidelines. The changes and their impact are presented in the following explanations and analysis.
1. Subjects Regulated: “Domestic Operations” Defined
In accordance with the Cybersecurity Law and the Draft Measure on Security Assessment for Outbound Personal Information and Important Data (the Draft Transmission Measure), personal information and critical data are required to be stored in China only if they are generated from the operations of Critical Information Infrastructure (CII) operators (based on the Cybersecurity Law) or all network operators (based on the Draft Transmission Measures) “during their operations within the PRC territory.” Such “operations within the PRC territory” are also referred to as “Domestic Operations,” which have been referred to in the preceding regulations and guidelines but have never been defined. Despite a debate on interpretation of such a term, the prevailing opinion in the industry was that it was limited to business operations conducted physically in China by business entities registered in China or via websites or applications hosted on servers in China. The Second Draft has defined “Domestic Operations” for the first time, but it is contrary to expectations. The definition states that a network operator without a registration in the territory of China may be viewed as engaging in “Domestic Operations” if it conducts business within China or provides products or services into the territory of China.
It further states that, when determining whether a network operator is conducting business within China or providing products or services into China, the following factors shall be considered:
- The language adopted for the transaction (Chinese or otherwise)
- The currency adopted for the transaction (RMB or otherwise)
- Whether the goods or services are distributed or delivered to China logistically
It fails to clarify whether only one or all of the above three factors need to be present, though, to support a positive determination. In any event, this definition seems to have a potentially overarching scope which may capture all foreign companies (even without Chinese subsidiaries and even if their websites are only hosted outside China) that have Chinese language websites and/or sell products or services into China where payments are settled in RIB. If implemented, this may have a chilling effect on cross-border transactions.
While extending its reach outside of China, the Second Draft has narrowed its reach inside China, clarifying that network operators residing within the territory of China will not be viewed as engaging in “Domestic Operations” if conducting business only with or providing products or services only to overseas entities or individuals, which does not involve personal information or critical data of any Chinese citizens.
Last but not least, same as the First Draft Guidelines, the Second Draft also affirmed the position adopted in the Draft Transmission Measures that all network operators (as opposed to just CII operators) will be subject to the data localization requirement.
2. Activities Regulated: “Data Cross-Border Transfer” Definition Updated
The definition of “Data Cross-border Transfer” is another key point for determining the applicability scope of the Cybersecurity Law. The Second Draft defines “Data Cross-border Transfer” as “one-time or continuous activities” of “providing” relevant information collected or created in China to foreign entities or individuals, via direct offering, or delivery via providing services or products. The Second Draft further states that the following circumstances are considered as “Data Cross-border Transfers”:
- Data provided to any subject that is located inside the territory of China but is not a subject under the jurisdiction of China, or that is not registered in China
- Data that has not been transferred outside China but has been visited and viewed by overseas entities and individuals (except for public information and webpage visits)
- Network operators’ internal data transfer involving personal information and critical data collected and generated from the network operator’s Domestic Operation
As one could tell, the above definition is much broader than everyone’s expectations. Certain data transfers within the territory of China may be considered as cross-border data transfers. However, it seems there is good news in the midst of the disappointed expectations.
The Second Draft has indicated that the transfer of data which is not collected or generated in China, and the transmission of data stored and processed domestically but collected and generated abroad shall not be considered as “Data Cross-border Transfer.” Apparently, foreign clients storing data in Chinese cloud servers shall not be caught by the rule restricting cross-border data transfer as long as such data is not generated or collected during any Domestic Operations.
3. Data Regulated: Definitions of “Personal Information” and “Critical Data” Refined
The Second Draft has referred to another draft of TC260 standards for the definition of “Personal Information” and “Sensitive Personal Information.” Such draft standards, namely, “Information Technology Security-Personal Information Security Specifications” (Draft Personal Information Specifications) are still in the drafting process with the most recent version released by TC260 on May 29, 2017. Exhibit A of the Draft Personal Information Specifications classified 13 categories of “Personal Information” and cited extensive examples (on a non-exhaustive basis) of each category. Exhibit B of the Draft Personal Information Specifications classified six categories of “Sensitive Personal Information,” also with non-exhaustive examples. Based on the Draft Personal Information Specifications and the Second Draft, the following information will most likely be viewed as “Sensitive Personal Information”: PRC ID number, bank account number, health record and biometric identification. It seems that the Second Draft intends to exempt the irreversibly de-identified personal information from the restrictions of the “Data Cross-border Transfer,” as indicated by Section 1.4 of Exhibit B.
The definition of “Critical Data” is still based on the non-exhaustive sector-by-sector list set forth in Exhibit A of the Second Draft, which does not have substantive changes compared to the same list in the First Draft. However, the Second Draft has emphasized that such data include both raw data and derivative data, while excluding any and all data that has been officially published by the government.
4. Assessment Procedures & Criteria: Overview
Similar to the Draft Transmission Measures and the First Draft Guidelines, the Second Draft contemplates two types of assessment procedures, namely, the Self-Assessment undertaken by relevant network operators themselves, and the Official Assessment undertaken by “competent authorities.”
According to the Second Draft, basically all network operators will need to undertake Self-Assessment when there is a Data Cross-border Transfer of “Personal Information” and/or “Critical Data” collected or generated during “Domestic Operations.” However, only some of them need to file their Self-Assessment report with the competent authorities, and only certain of them need to go through the Official Assessment and obtain the approval from the competent authorities.
The assessment criteria was slighted modified in the Second Draft compared to the First Draft: (i) “lawful and appropriate” was amended as “assessing whether the purpose of the proposed transmission is lawful, appropriate and necessary”, and (ii) “risk controllability” was rephrased as the “security risks.”
A flow chart included in the Second Draft show an overview of this whole process:
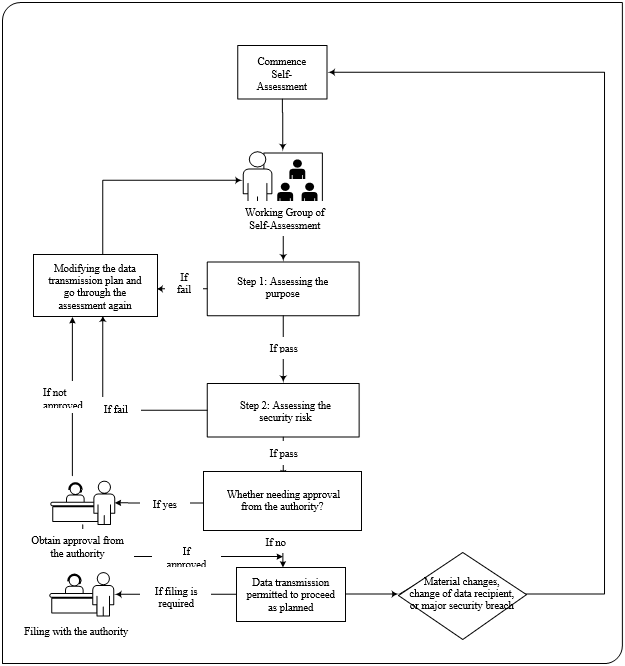
Source: Section 4.2.1 of the Second Draft
5. Assessment Procedures: Self-Assessment
The Second Draft has provided certain useful clarification on the operating details of the Self-Assessment.
First, it has clarified that Self-Assessment shall be undertaken per each instance of transfer, provided, however, that consecutive instances of transfer occurring within one year with the same purpose of transfer and same data recipient, and substantially similar scope, type and volume of data, can be viewed as one single instance and covered by just one assessment report.
Second, it has made a rule for identifying the responsible party when multiple parties are behind the same transfer event (such as where cloud hosts or outsourced IT service providers are involved). In such an event, according to the Second Draft, the party that “initiated” the data transmission request shall be responsible for the Self-Assessment. For example, if a cloud service client proactively asks a cloud service provider to carry out a cross-border data transfer, the cloud service client shall assume responsibility for and the cloud service provider shall cooperate with the cloud service client to carry out the Self-Assessment, and vice versa.
Third, the Second Draft has also added some formalities for the Self-Assessment. It requires that, as the first step, the business team of the network operator shall formulate a data transfer plan (Data Transfer Plan) which shall cover relevant information on the personal information, critical data proposed to be transferred, the information system involved, and the information on the recipient and transferor. Afterward, the network operator shall form a working group to review the Data Transfer Plan and prepare the Self-Assessment Report. Such a working group shall consist of members from legal, technology and management functions of the network operator. The Self-Assessment Reports are required to be retained for at least two years (the First Draft required a longer period, i.e., five years). It also seems to suggest that network operators may engage third-party professional institutions to prepare the Self-Assessment Report.
6. Assessment Procedures: Filing With Competent Authorities and Official Assessment
The Second Draft, for the first time, required the network operators under certain circumstances to file Self-Assessment Reports with the competent authorities. Such circumstances are largely the same as those that would trigger the Official Assessment under the Draft Transmission Measures, with slight modifications and specifically as follows:
- Self-Assessment conducted by CII operators
- The volume of Personal Information proposed to be transferred out of China within one year exceeds the limit set by the competent authority (note: this has replaced the hardline rule of “500,000 data subjects” as relevant for Personal Information, and “1000 GB” as relevant for other data, as proposed in the Draft Transmission Rule)
- Data containing information concerning nuclear facilities, chemistry and biology, national defense and the military, demographic health, large-scale engineering projects, the marine environment or sensitive geographic information, etc.
- Data relating to CII cybersecurity information such as system vulnerabilities or security measures
- Situations where national security, economic development or public interest may be otherwise affected
The triggering events for Official Assessment cover all above items and three additional scenarios: (i) subject to a large number of user complaints or reports; (ii) suggested by national trade associations, or (iii) otherwise viewed necessary by competent authorities.
“Competent authorities” referred to in relation to the security assessment for cross-border data transfers include both CAC and the government agency in charge of the industry in which the network operator operates. Such authorities have the right to conduct review through “remote monitoring” and “site inspections.” The competent authorities will form a “working group” to prepare an Official Assessment report and will also take into consideration the opinions offered by an “expert committee.” A final decision will be made in writing and the network operator will be notified. No timeline is specified for such Official Assessment process or each step thereunder.
7. Other Developments Under the Second Draft
The Second Draft, like the previous rules, has required that network operators shall expressly notify the purpose, type, recipient and possible risks to individuals whose personal information is to be transferred abroad prior to obtaining their consents. It has further specified that, in the event of a change in a network operator’s privacy policy or recipient or a major change in export purpose, scope, type, amount or risk, consents must be obtained again from these individuals. However, the Second Draft provides that transferring Personal Information on individuals’ proactive basis (including making international phone calls, sending international emails, conducting international instant messaging, conducting cross-border transactions through internet) or transferring Personal Information that has been already legitimately disclosed to the public shall be construed as having obtained consent.
The Second Draft also explicitly requires that both the data transferor and the data recipient shall retain the relevant data transfer logs for at least two years.
The following changes have been made in the Second Draft in relation to the evaluation of “impact of data”:
- “Limited Amount of Sensitive Personal Information” is further quantified as Sensitive Personal Information accounting for less than 50 percent
- The hardline rule of “500,000 individual data subjects within one year” and “critical data with volume exceeding 1000 GB” each as a factor to adjust upward the impact class of the data has been replaced with uncertain thresholds to be further determined by the competent authorities
8. Outlook
The Cybersecurity Law has been effective for four months; however, the data localization requirement as one of the rules established thereunder that would likely impact foreign businesses, had not yet been implemented. The delay in implementation was largely due to the pending implementation rules and standards. The Draft Transmission Measures had been expected to bridge this gap. Since the first version of the Draft Transmission Measures were published on April 11, 2017, discussions had been held by the legislators with industry representatives and a second draft had been circulated to the closed circle in late May with a rumor that the final version would be out soon; however, to date no updated version has ever been officially published and no clear timetable for the final version has ever been announced. Instead, the Second Draft was produced and published on the last day of August 2017, which seems to signal that Chinese regulators have been taking a more prudent approach to delegate this issue to standardization committee with more technical expertise. However, it is still unclear when the operating details created by such guidelines will be finalized and come into effect.
The material contained in this communication is informational, general in nature and does not constitute legal advice. The material contained in this communication should not be relied upon or used without consulting a lawyer to consider your specific circumstances. This communication was published on the date specified and may not include any changes in the topics, laws, rules or regulations covered. Receipt of this communication does not establish an attorney-client relationship. In some jurisdictions, this communication may be considered attorney advertising.

